LockBit Takedown and Resurgence

LockBit Takedown and Resurgence
What Happened?
In a coordinated effort by National Crime Agency, Europol and multiple other internation law enforcement agencies dealt a significant blow to the operations of the LockBit ransomware group. Dubbed Operation Cronos, this multi-agency initiative led to the seizure of LockBit’s dark web portal and in a swift transition, the portal was repurposed into a knowledge base housing critical information for victims and stakeholders. As part of the operation, law enforcement agencies dismantled numerous servers associated with LockBit, seized multiple cryptocurrency wallets linked to illicit activities, and recovered a substantial number of decryption keys.
LockBit Background:
LockBit’s emergence in 2019 marked the beginning of its evolution into a nefarious Ransomware-as-a-Service (RaaS) operation. Since late 2021, LockBit has maintained a relentless pace, consistently targeting approximately 200 victims per quarter. It has more than 2,300 victims documented within its dark web portal, however, it’s important to note that these figures may not encompass all victims, as some may have engaged with LockBit offline, outside of its dark web portal.
LockBit coded in C/C++ utilizes a customized AES+ECC cipher, employing a unique encryption method that targets only the initial 4 KB of each file. This strategic approach renders the files unstable, speeding up the attack and providing defenders very less time to stop the attack. Its encryptor has undergone numerous iterations and developments, evolving into a highly sophisticated weapon in the realm of cybercrime.
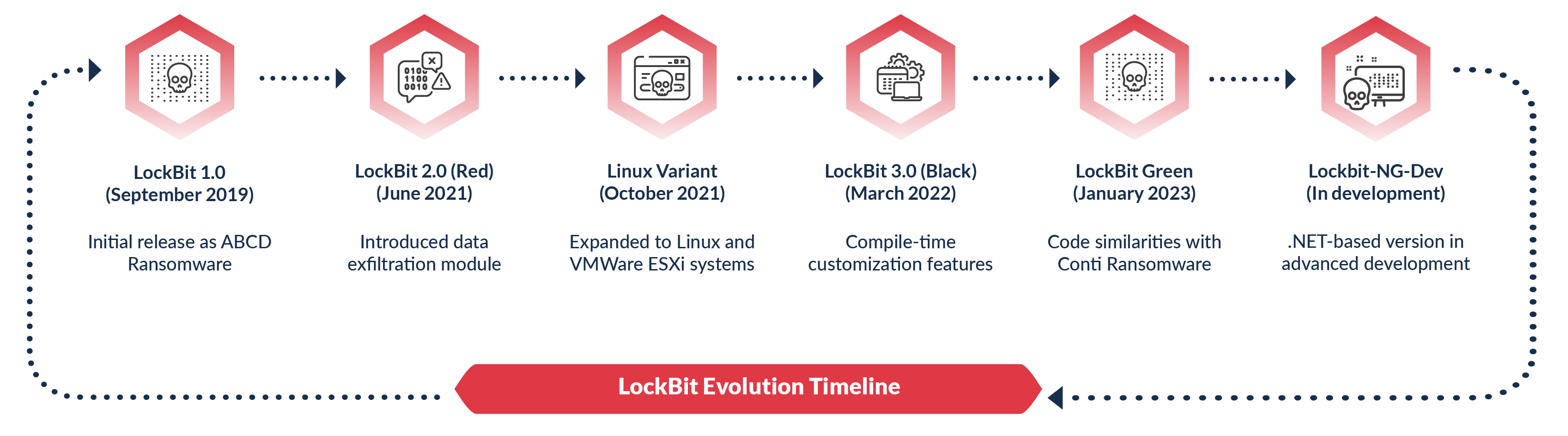
LockBit Evolutionary Journey
- LockBit 1.0 <September 2019>: Emerged as the initial iteration, encrypting files with the “.abcd” extension, formerly recognized as the ABCD Ransomware.
- LockBit 2.0 (Red) <June 2021>: Introduced the exfiltration module, offering a choice between rclone and Stealbit, alongside the option to exfiltrate data to local disks or cloud storage.
- LockBit 3.0 (Black) <March 2022>: Introduced compile-time customization features, empowering operators to manipulate system settings such as safe mode and cipher selection.
- Linux Variant <October 2021>: Expanded its reach to Linux and VMWare ESXi Systems, diversifying its target landscape.
- LockBit Green <Jan 2023>: Exhibited code similarities with the defunct Conti ransomware, showcasing a nuanced evolution in its development trajectory.
Moreover, a forthcoming .NET-based iteration, Lockbit-NG-Dev, at an advanced development stage was also discovered in recent attack. Each of these versions aimed to improve encryption strength and evade detection.
How It Happened:
LockBit hack is purported to be the exploitation of a PHP flaw either CVE-2023-3824, a buffer overflow leading to RCE or a zero-day in PHP. The exploitation enabled Enforcement agencies to take over their dark web portal, victim’s admin server and chat servers running vulnerable PHP version. The agencies seized LockBit’s site and skillfully converted it into a knowledge base maintaining its distinctive LockBit aesthetic. Their operation resulted in the dismantling of 28 servers, the recovery of over 1,000 decryption keys, and the acquisition of the platform’s source code. Additionally, they effectively blocked 200 crypto accounts associated with illicit activities and flagged over 14,000 rogue accounts worldwide for removal. Additionally, Agencies have destroyed all StealBit proxy servers, LockBit’s exfiltration platform, severely limiting its functionality.
One notable aspect of Operation Cronos was the access gained to LockBit’s affiliates panel. Federal agencies leveraged this access to gather valuable intelligence, including affiliate nicknames, chat histories, Bitcoin wallet addresses, and IP information. Around 190 affiliates were discovered, and outreach efforts were initiated with affiliates, marking a proactive approach to engage with individuals connected to criminal enterprises.
LockBit Resurgence:
LockBit resurfaced on 24th Feb with a new tor site and a list of victims. It managed to restore itself from backup servers which didn’t had vulnerable PHP versions. In a follow-up message, LockBit claimed that the agencies targeted its infrastructure following a ransomware attack on Fulton County in January, which potentially compromised sensitive documents relevant to upcoming U.S. elections. They called for more frequent attacks on the “.gov sector” and revealed that the authorities obtained only 2.5% of decryption keys.
Acknowledging their previous lapses in patching vulnerabilities, the group has pledged to enhance their security measures proactively. In response to evolving threats, they have refined the trial decryption process, opting to avoid storing keys on the portal servers to mitigate potential risks. Additionally, the group has issued a call-to-action for new affiliates to join their ranks, aiming to bolster their operational capabilities and expand their network.
What Next:
- If law enforcement agencies effectively leverage the data obtained on LockBit’s affiliates to disrupt their activities and prevent malicious intentions, the Ransomware-as-a-Service (RaaS) market could experience a substantial downturn. The fear of potential exposure and prosecution may deter individuals from participating in such illicit operations, thereby reducing the overall threat posed by RaaS entities.
- With multiple arrests and indictments already underway and expected to continue, particularly those closely associated with the LockBit gang, the group’s operational capacity may diminish significantly. The apprehension of key members and affiliates could disrupt their organizational structure and impede their ability to carry out ransomware attacks effectively.
- The intricate internal workings and operational mechanisms of LockBit provide valuable insights for law enforcement agencies to counteract similar ransomware operations effectively. By understanding the modus operandi and vulnerabilities inherent in LockBit’s infrastructure, authorities can develop targeted strategies to disrupt and dismantle similar cybercriminal networks.
- LockBit’s compromised operations have undoubtedly eroded the trust of its affiliates. Should its resurgence prove ineffective or insufficient to regain confidence, there is a substantial possibility that other Ransomware-as-a-Service (RaaS) operators will step in to fill the void.
Event Timeline:

Author: Ankit Mani





