HivePro Uni5

The Uni5 platform elevates traditional vulnerability management to holistic threat exposure management by identifying your enterprises' likely cyber threats, fortifying your weakest controls, and eliminating the vulnerabilities that matter most to reducing your enterprise risks.

Consolidate Security Tests, Assessments, and Workflows for Enhanced Risk Management

The Uni5 platform elevates traditional vulnerability management to holistic threat exposure management by identifying your enterprises' likely cyber threats, fortifying your weakest controls, and eliminating the vulnerabilities that matter most to reducing your enterprise risks.
Build your Cyber Resilience
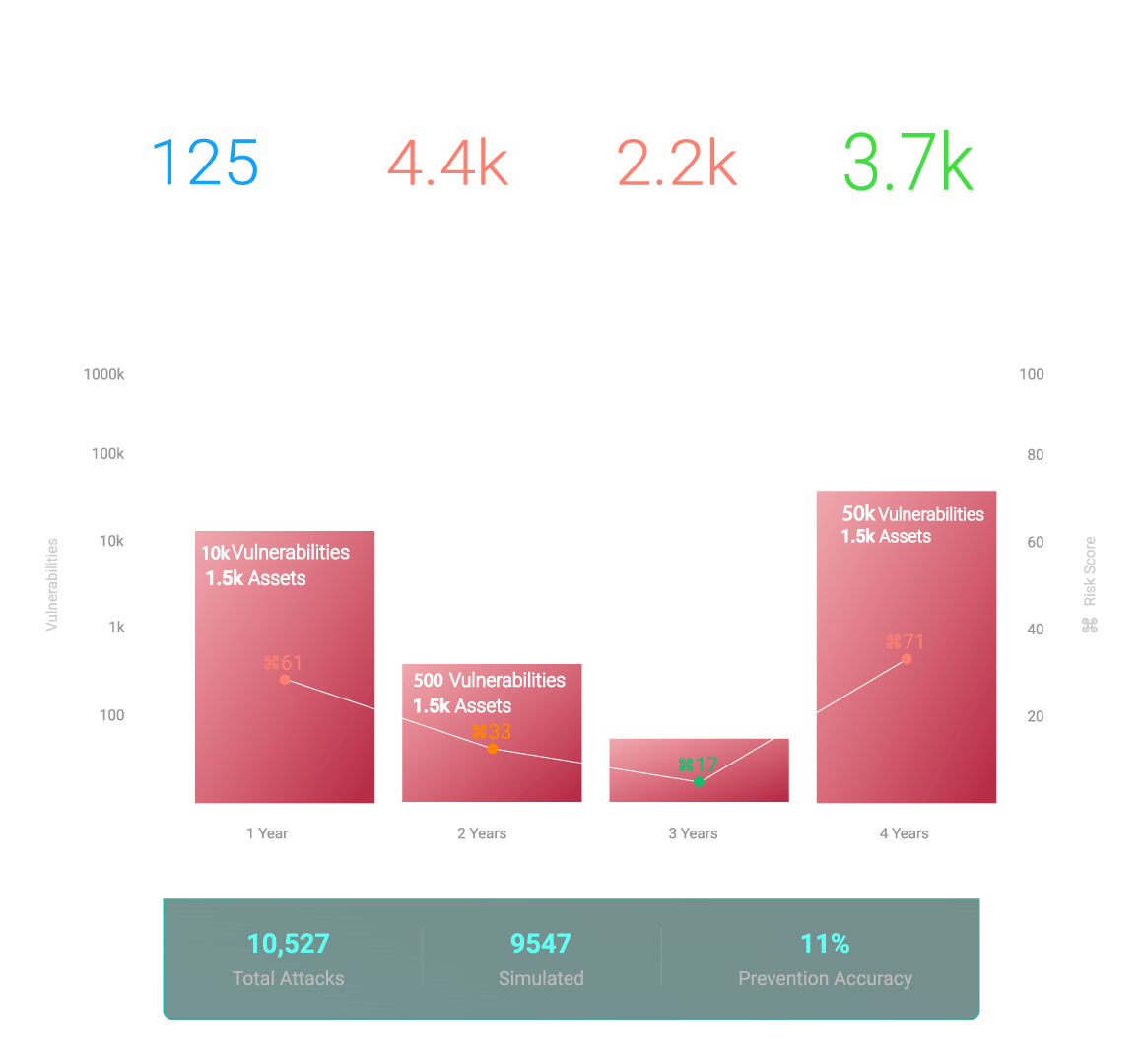
Your HivePro Uni5 Journey
Minimizing your threat exposure and outmaneuvering cybercriminals requires enterprises to know their terrain, and the “attacker’s perspective” well. HiveUni5 platform provides wide asset visibility, actionable threat and vulnerability intelligence, security controls testing, patch management, and in-platform, cross-functional collaboration. Close the loop on risk management with auto-generated strategic, operational, and tactical reports.
Current Problems in Vulnerability Management
Current Problems in Vulnerability Management
If assets (like servers, computers, or applications) are not discovered, they might not be secured or patched, making them vulnerable to attacks. A gap means incomplete risk assessments, hidden costs, higher risks of a breach, and potential non-compliance, which can result in fines or sanctions.
If assets (like servers, computers, or applications) are not discovered, they might not be secured or patched, making them vulnerable to attacks. A gap means incomplete risk assessments, hidden costs, higher risks of a breach, and potential non-compliance, which can result in fines or sanctions.
Most vulnerability prioritization tools on the market fail to consider the total sum of true enterprise risks, including but not limited to: asset context and criticality, environmental factors, vertical factors, threats, exploitability and compensating controls–yielding inadequate priorities.
Most vulnerability prioritization tools on the market fail to consider the total sum of true enterprise risks, including but not limited to: asset context and criticality, environmental factors, vertical factors, threats, exploitability and compensating controls–yielding inadequate priorities.
Security functions have both siloed tools and manual hands gathering critical vulnerability, threat, IoC and patch intelligence. Without a unified, consistent and trustworthy view of the intelligence that matters, blind spots are inevitable, risks increase, breaches become likely.
Security functions have both siloed tools and manual hands gathering critical vulnerability, threat, IoC and patch intelligence. Without a unified, consistent and trustworthy view of the intelligence that matters, blind spots are inevitable, risks increase, breaches become likely.
IT Operations require clear context and evidence-rich remediation guidance for all escalated Security alerts and proposed fixes; however, there is never enough. This yields a stagnated remediation backlog, creates friction between functions, and prolongs threat exposure.
IT Operations require clear context and evidence-rich remediation guidance for all escalated Security alerts and proposed fixes; however, there is never enough. This yields a stagnated remediation backlog, creates friction between functions, and prolongs threat exposure.



Eliminate Remediation issues with HivePro Uni5
Minimize Your Threat Exposure From Code-to-Cloud On One Unified Platform
- Automated Asset Discovery to Surface Asset Blind Spots
- Assigned Business Asset Criticality & Sensitivity
- The strength of Compensating Controls & Coverage
- Latest Threat and Vulnerability Intelligence
- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges


- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges
- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges


Eliminate Remediation issues with HivePro Uni5
Minimize Your Threat Exposure From Code-to-Cloud On One Unified Platform
- Enterprise and Environmental and Threat risks
- Strength of Compensating Control(s)
- Proximity of Likely Threats
- Latest Threat and Vulnerability Intelligence
- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges


- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges
- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges


Eliminate Remediation issues with HivePro Uni5
Minimize Your Threat Exposure From Code-to-Cloud On One Unified Platform
- Alert Asset Owners Regarding Asset Risks Decisions
- Escalate findings and remediation options to ITOps & DevOps
- Automate patches with integrated patch intelligence and management tools
- Generate Customizable Reports for technical and non-technical stakeholders
- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges


- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges
- Historical security assessments, scans and tests
- Vulnerability Intelligence, Threat Intelligence, IoC Intelligence, Patch Intelligence
- Environmental Context, Business Context, Proximity of Threats, Compensatory Controls
- Asset Criticality according to customizable criticality scores and score ranges


Target High-Risk Vulnerabilities.
Eliminate Likely Threats.
Prevent Attacks.
Automated Tools Integration
HivePro Uni5 supports over 27 well-known Asset Management, ITSM, Vulnerability Scanners and Patch Management tools out of the box, allowing organizations to utilize their existing investments.






Single Pane View For Complete Threat Exposure Management.

Reduce Your Business Risks With HivePro Uni5's Threat Exposure Management Platform
Alleviate the tool sprawl immediately by connecting to your scanners, attack surface management, ITSM, and ticketing tools of choice and immediately experience what threat exposure reduction and streamlined remediation should look like.






