Home
PLATFORM OVERVIEW
Build your Cyber Resilience
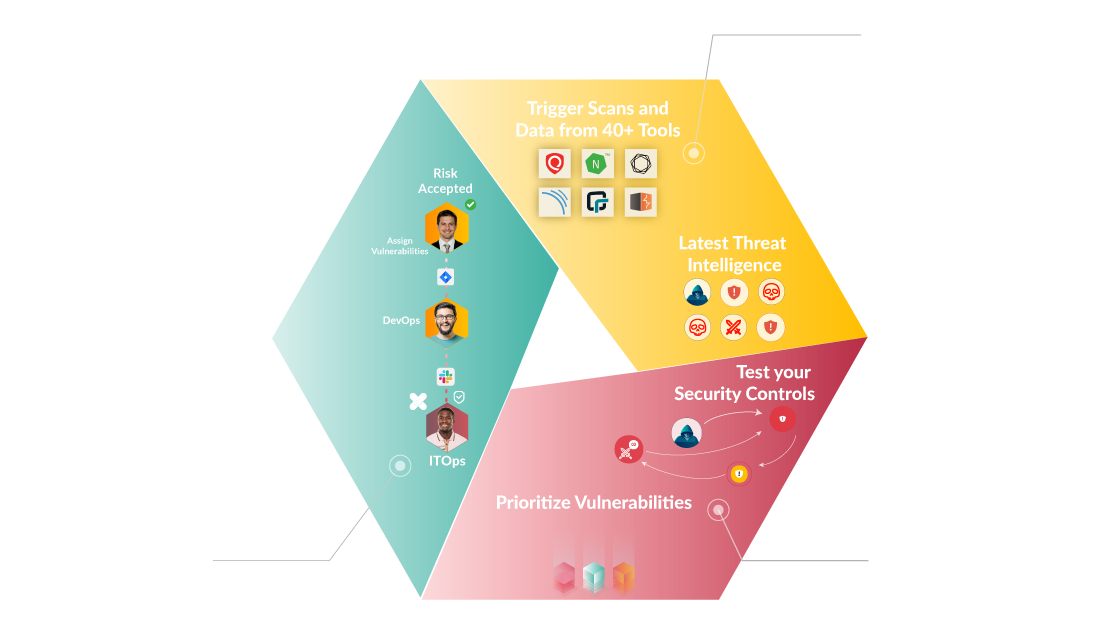
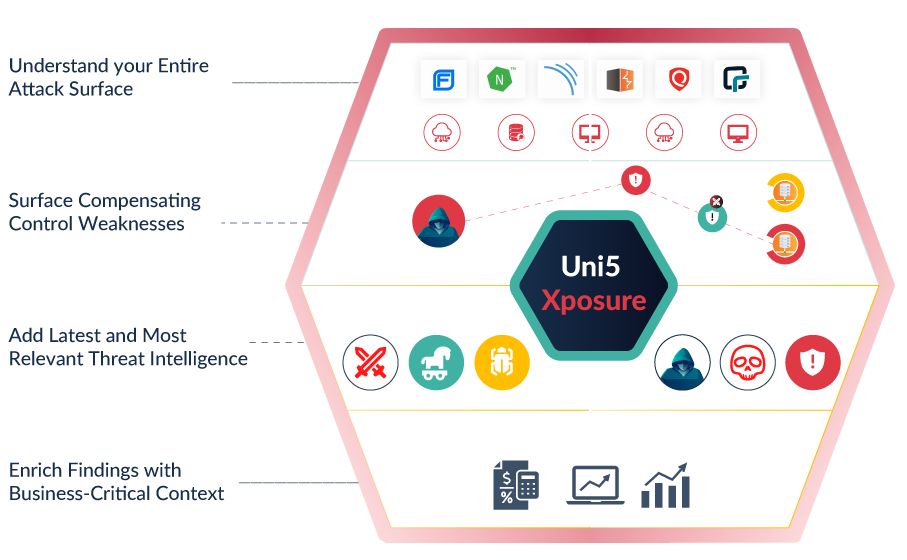
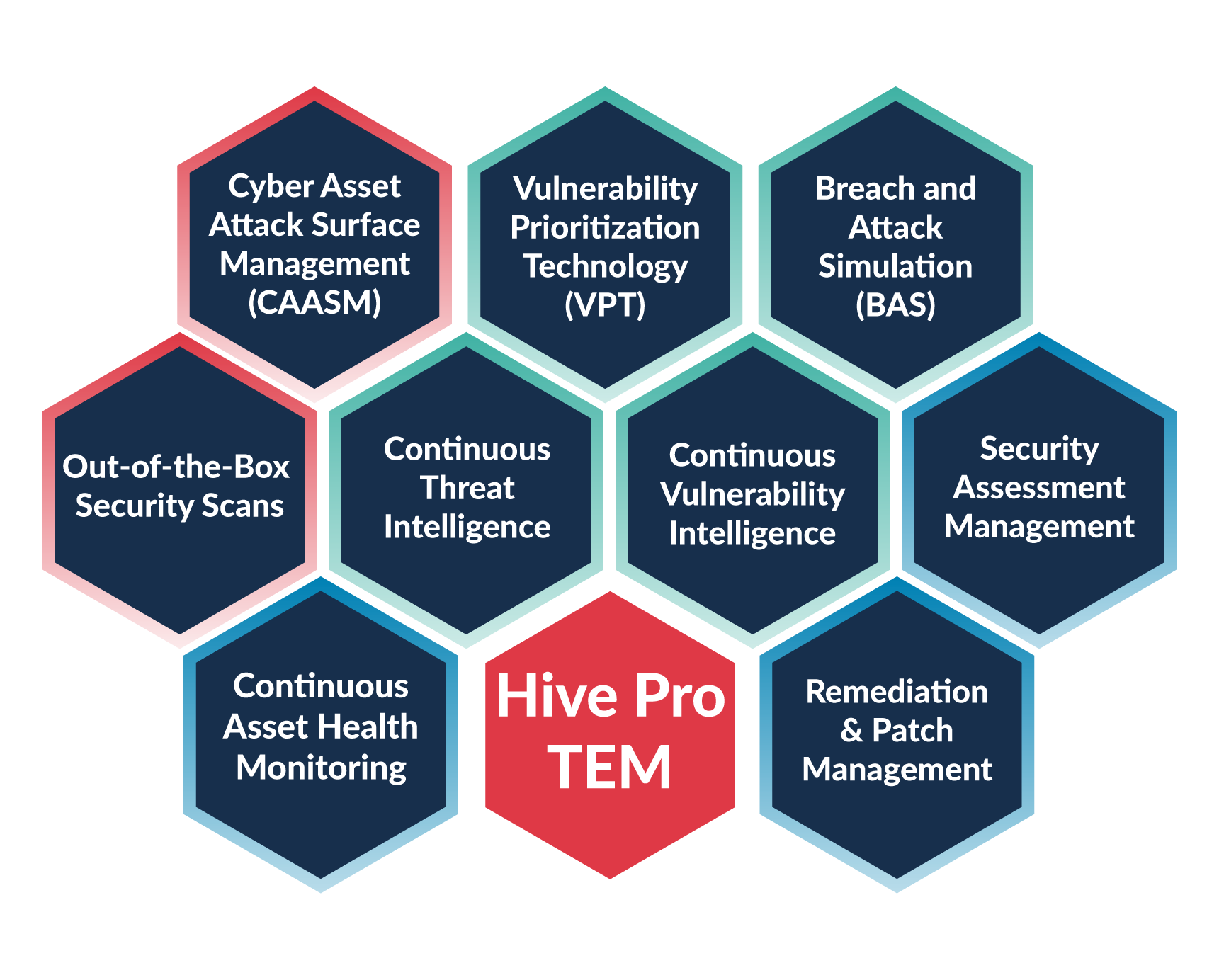
Hive Pro TEM: All-In-One Platform
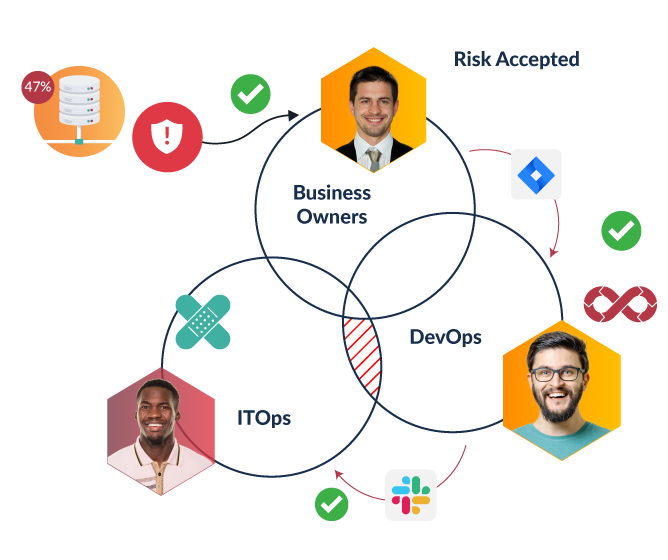
Hive Pro: Threat Exposure Management (TEM) is an all-in-one, fully-integrated platform that provides wide asset visibility, actionable threat and vulnerability intelligence, security controls testing, patch management, and in-platform, cross-functional collaboration. Close the loop on risk management with auto-generated strategic, operational, and tactical reports through our TEM platform.
Optimize Cybersecurity Investments with Effective Threat Exposure Management
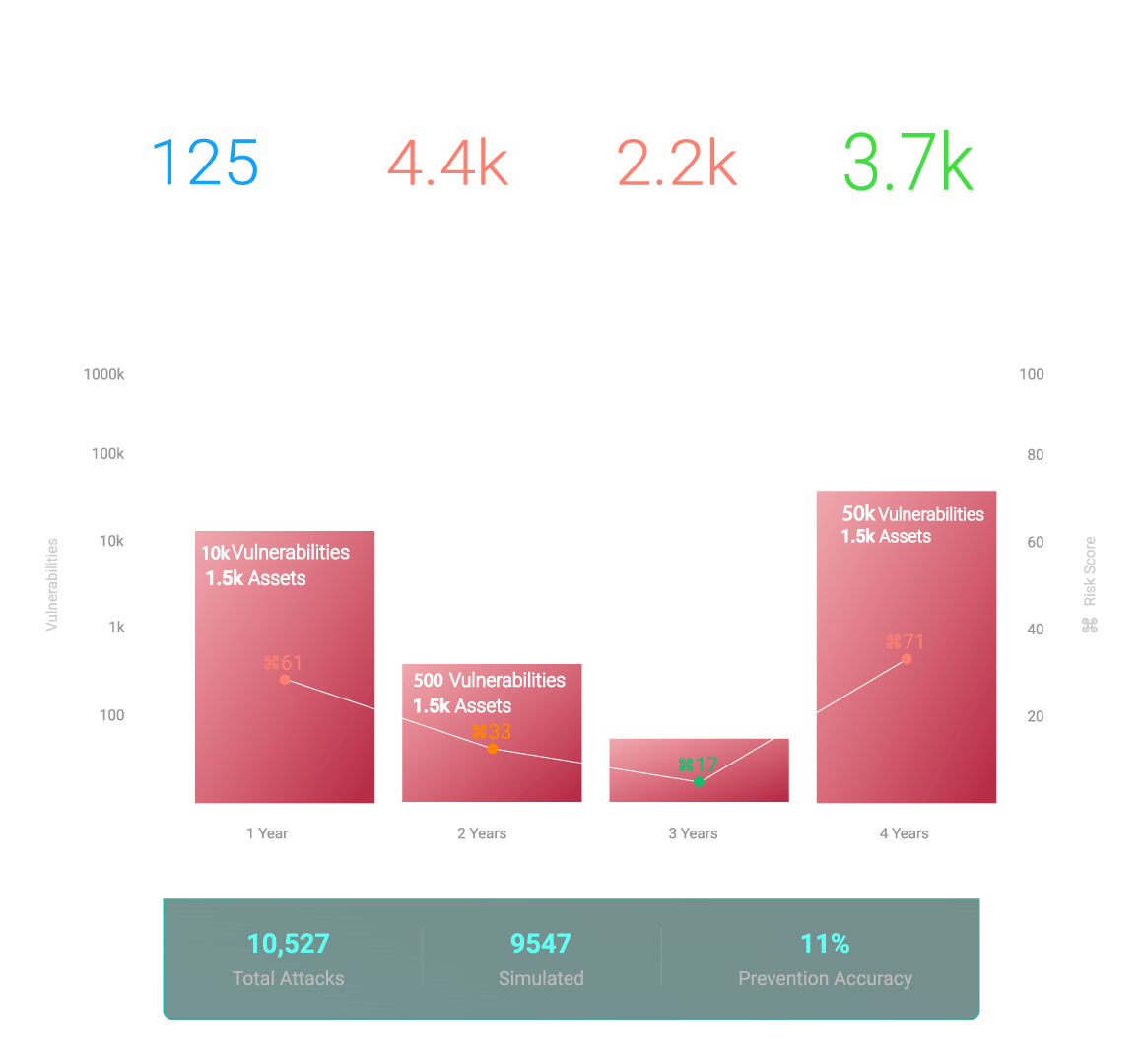
Rapid Remediation: 4X Faster
Quickly identify and resolve vulnerabilities to outpace your competition and ensure your business is secure.
Protect Business-Critical Assets: 70% Reduced Risk
Keep your most important assets safe from cyber attacks with Hive Pro's advanced security features.
Optimize Operations: 2X Efficiency Leap
Experience unprecedented efficiency improvements in your daily operations with Hive Pro's cutting-edge optimization solutions.
Key Benefits
Book a free demo and find out more about how Hive Pro can double your operational efficiency
Resources
Time to Level Up! Get the Whitepaper for In-Depth Insights on Enhancing Vulnerability Management.

Industry Recognition


Testimonials
Why Our Customers Love Us
Build your Cyber Resilience
Embrace Hive Pro’s cutting-edge All-In-One Threat Exposure Management Platform for improved vulnerability management, fortified security, and seamless collaboration. Upgrade your cybersecurity resilience now!