What is Continuous Threat Exposure Management (CTEM)?

What is Continuous Threat Exposure Management (CTEM)?
Introduction
Why don’t all of your tools in your SOC talk?
This isn’t a rhetorical question. We know that cybersecurity is a capital industry. We know that human nature inherently plays its part in division too. However, what we cannot answer still is why the cybersecurity industry cannot agree to collaborate on its overall strategic objective: to protect organizations from cyber-attack to the best of their ability. The inherent unity required here is a growing trend in the cybercrime world. Lone-threat actors are forming united fronts. One would assume that given our fight against a common aggressor, we would work together to elevate security. This is our hope, at least.
Perhaps the concept of the cybersecurity mesh as termed by Gartner carries in it the blueprint towards the ideal—one security language, distributed action across the tool landscape. And if that be so, then a part of that blueprint, a building block if you will, would be continuous threat exposure management.
“CTEM program is a set of processes and capabilities that allow enterprises to continually and consistently evaluate the accessibility, exposure and exploitability of an enterprise’s digital and physical assets.”
- Gartner
Continuous Threat Exposure Management (CTEM)
Continuous threat exposure management is a programmatic approach geared towards cybersecurity end-users. It finds its inception in Gartner’s reaction to the increasing potential of threat actors unaffected by the current state of (holistically inadequate) cybersecurity controls. Right now, the current state of threat management yields “rarely actioned reports and long lists of generic remediations” as the attack surface expands, according to Gartner. The goal of this program is to help end-users ascertain how: accessible, exposed, and exploitable their digital assets are to cyber threat actors so as to ensure better risk management.
Gartner proposes 5-steps in a CTEM program:
Scoping, Discovery, Prioritization, Validation, Mobilization

We simplified this 5-step program into a 3-step program, combining and re-naming the following:
- Scoping & Discovery: “Contextualize”
- Prioritization & Validation: “Prioritize”
- Mobilization: “Resolve”

Contextualize:
To consider something in the situation/context within which it is placed.
Here, the something, or somethings are your assets, the situation/context your organization.
This means that an organization’s SOC team, after conducting a discovery exercise on all of their assets, must classify their most critical assets as determined by the impact that any disruption would have on their organization’s operations. Only after understanding the inherent meaning and importance of their assets can they do anything with the tools in their environment. Asset discovery/management tools do discovery well, but they are a long shot from assessing the true and critical nature of assets without customer input. Discovery exercises will also yield several areas for improvement, and this is where problems surface. Organizations will have long lists of potential remediations, but not enough resources and little diplomatic agreement cross-function to resolve them all. Priorities are necessary.
Prioritize:
So, what matters most?
NIST 800-30 2002 gives us a clear risk equation to abide by:
Risk = Threat x Vulnerability x Probability X Impact / Controls in place
Organizations can better ascertain how vulnerable their assets are and the impact downtime will have on them considering compensating controls in comparison to determining threat and probability.
Who are the threat actors to look out for, why do they matter, and how likely is it that an organization would be a victim?
The answers to all of these questions are results of whatever intelligence an analyst or team of analysts can digest in a given frame of time from every (siloed) tool available paired with their confidence and “gut feel”. Even then a long list of remediations requires another intelligence filter that yields agreed-upon priorities. We think more data is necessary. Better correlation. More evidence. Stronger confidence. Predefined based severity scores without context simply doesn’t cut it. Without better qualification of threat and probability, risk cannot be confidently ascertained.
Resolution:
Only with more accurate data regarding the urgency and severity of threats can prioritized resolution be defended and better communicated to all stakeholders.
Hive Pro’s mission is to support the customer CTEM journey from understanding their digital environment to protecting it through a threat and risk-informed approach.
HivePro Uni5
HivePro Uni5 is a Threat Exposure Management Platform that supports our mission by contextualizing your business-specific threats, prioritizing your vulnerabilities and promoting actionable paths to resolution, on a continuous basis.
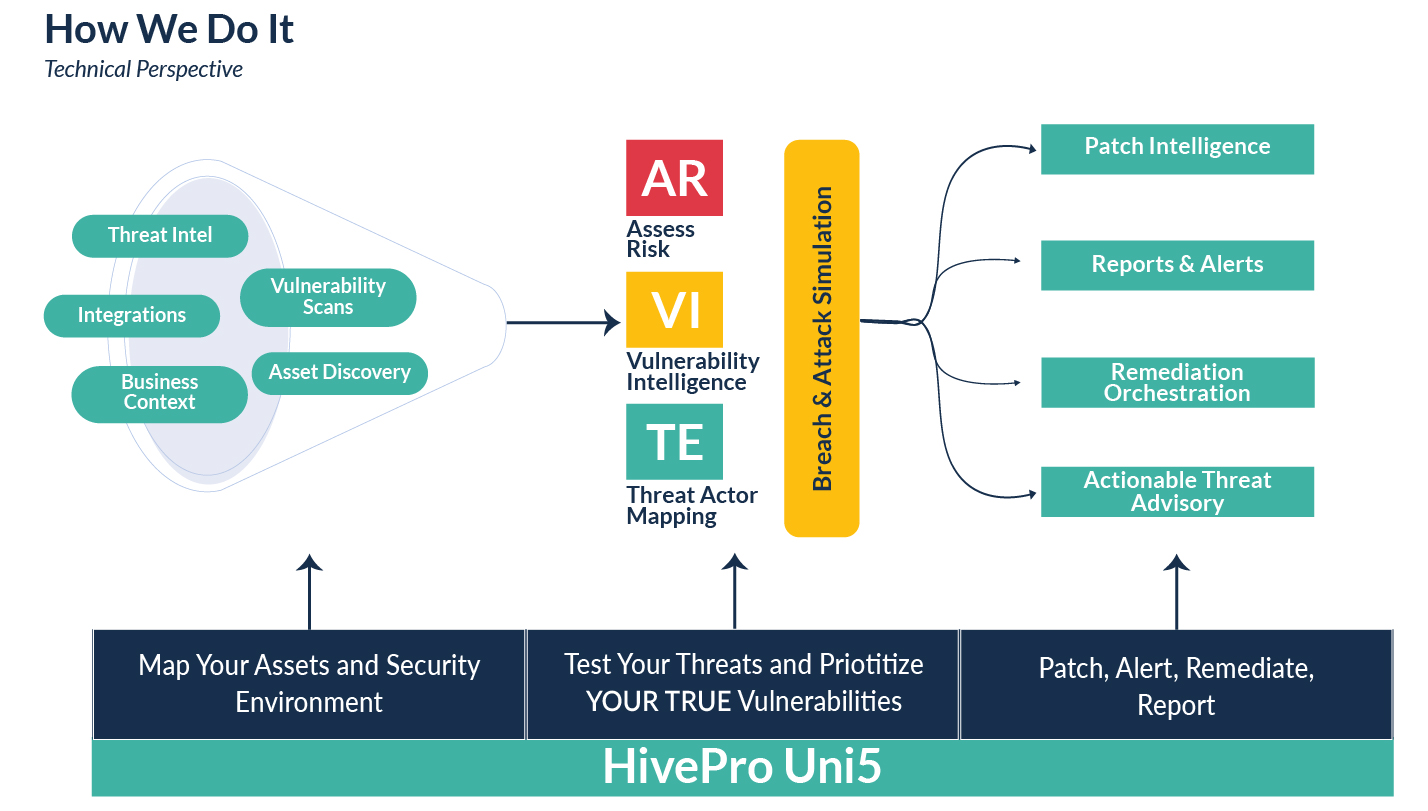
HivePro Uni5 takes into account your entire digital environment, our ever-expanding threat, actor and vulnerability intelligence and your business context to assess and prioritize your asset risks in our platform. We test the yielded prioritizations against our breach and attack simulation tool to help red and blue teams build confidence in our tool and in their resolution process. From your prioritized vulnerabilities, you can then initiate patching, reports/alerts, provide threat advisories, and/or orchestrate any other kind of remediation. This orchestration requires us to help you see the bigger picture through strong integrations across your tool landscape and features to facilitate decision-making. Otherwise, all we would have are unrealistic, siloed, and tool-centric approaches

And we stand by our earlier statement in unifying the security industry through our platform to win the fight against our common aggressor: cybercrime actors. Our many integrations across asset management, vulnerability management, ITSM and patch management fit a good majority of the tools involved in the CTEM story. From the data and integration capabilities provided combined with our own data, research, and toolset, we help tell the threat and risk management story with various reports that can be generated at any time and for free through HivePro Uni5.
“The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand, and architecture teams can act upon.”
- Gartner

With HivePro Uni5, there’s no need to sunset your tools to pick up ours. We seek to be great integrators and vulnerability remediators.
Our goal is to provide a consistent, actionable and understandable security posture and remediation improvement plan(s) for all of our customers. With our intelligence, customers can continuously and consistently evaluate the accessibility, exposure and exploitability of their digital assets, and generate actionable reports for cross-functional stakeholders.
The purpose of HivePro Uni5 is to optimize your security posture by contextualizing your business-specific threats, prioritizing your vulnerabilities and promoting actionable paths to resolution. This is continuous threat exposure management at its core.




